Maximize Password Cracking Ability with OneRuleToRuleThemAll

About six months ago I discovered a few GREAT wordlists that have drastically increased my password cracking ability. See my post here. I have taken this new password cracking ability and maximized 10x with hashcat rules. Hashcat rules change the words in a wordlist to fit common password conventions such as changing an "a" to an "@" or an "E" to a "3." There are countless published rules out there but OneRuleToRuleThemAll incorporates 4 of the most effective.
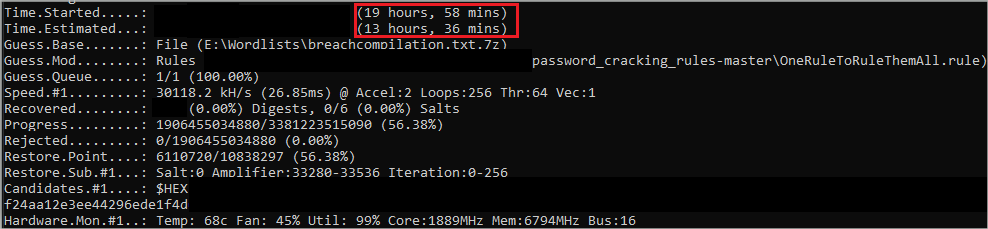
With a beast of a wordlist like BreachCompilation AND OneRuleToRuleThemAll, you are inching towards Thanos-level power. That is, as long as you are willing to dedicate some computer power and time to cracking! I am currently 24 hours in with 44% of words still to go with an NVIDIA GeFORCE GTX 1660 Super GPU on a few passwords I am testing.
The syntax of the hashcat command to run with OneRule is as follows:
hashcat.exe -m $HASHCODE -a 0 hashes.txt Path\To\Wordlists\wordlist.zip -r location\of\ruleset.rule
Good luck and happy cracking!!
References: