How I Conduct External Reconnaissance for Penetration Testing Engagements

External reconnaissance is a very important part of a penetration testing engagement. This sets the tone for the engagement and provides essential insight regarding the applications, infrastructure, and people of the client organization. I use dozens of different resources for external recon. However, before firing up any actual recon tools, I always check out the client's main website to get a sense of the type of business the organization conducts. What kind of services or products do they provide? What compliance frameworks (HIPAA, PCI-DSS, FERPA, etc.) apply to them? Would these services need a lot of publicly facing applications? How do they interact or serve their clients or customers? How old is the organization? Did this company have any recent publicly reported breaches. All of these questions help you identify potential vulnerabilities or gaps In their security. Creativity and curiosity is essential! After asking yourself these questions, check out these tools to find valuable organization information:
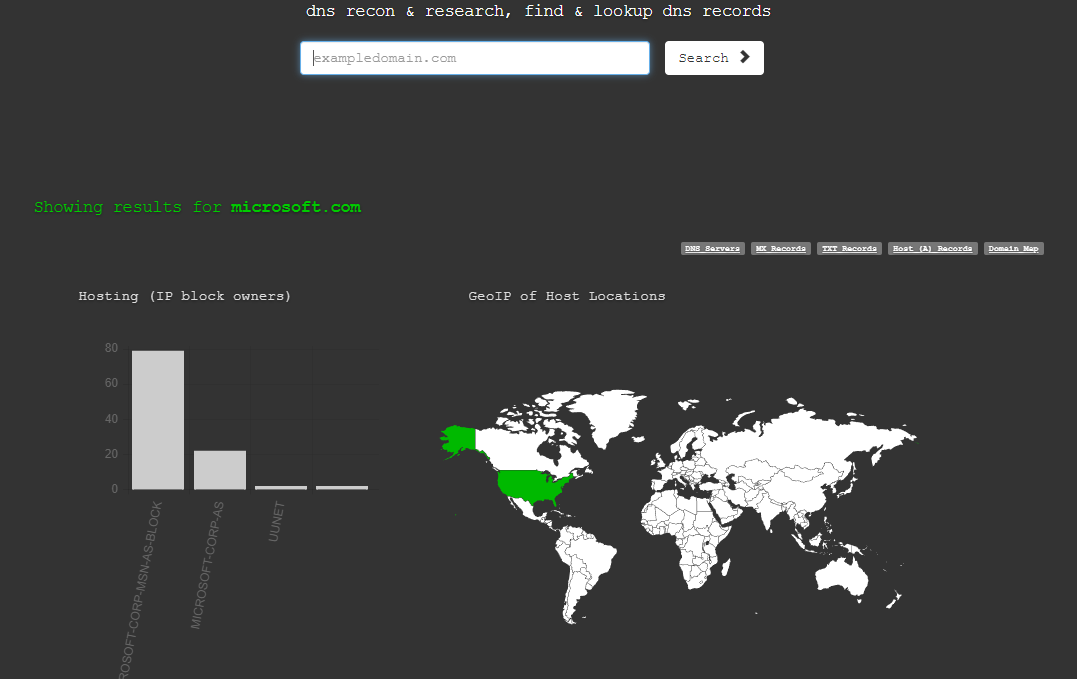
- DNS Dumpster
This site is a great starting point for DNS subdomain reconnaissance. Businesses will often create and forget subdomains. Identifying long forgotten subdomains provides you and your client insight into the full external threat surface of an organization. Look for subdomains such as "vpn.domain.com" or "rdp.domain." Subdomains like these indicate potential initial intrusion points.
2. Phonebook.cz
After doing some subdomain research, you should move into email identification. Phonebook.cz provides an incredible search function for emails and subdomains. Provide the target domain, and it will return email addresses, URLs, and subdomains.
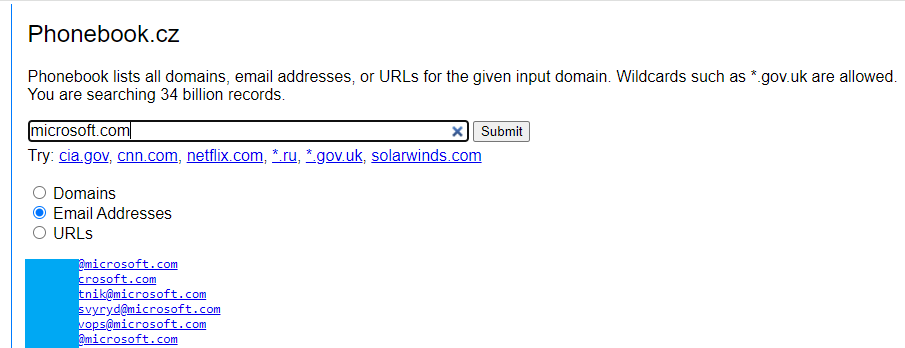
*At this point, you will notice that with just two public information sources, you can begin to get a very rich picture of an organization.
3. Censys.io
Once you find those subdomains on DNS dumpster you will want to find their corresponding IP address and enter it in censys.io. Censys.io will show you open ports on the asset and some other interesting certificate information. It also makes it easy to find other assets within the organization.
4. Wappalyzer
Wappalyzer enumerates the targets organization's applications and web frameworks in use. Once you identify the web technology in place, do some research on common vulnerabilities associated with the technology and identify attack vectors.
