LDAPDOMAINDUMP.py ---> Domain Admin

This month on an internal penetration test I obtained domain administrator privileges in under 10 minutes with the help of a simple tool called LDAP Domain Dump.
On every internal penetration test, the first thing I do after collecting credentials is run the tool LDAP Domain Dump. This tool enumerates and extracts all read-only information from a domain controller. In this case, I found a cleartext credential for a privileged account in the Description field of the Active Directory object. With a quick crackmapexec check, I discovered that this account has domain admin privileges. Here's how I did It:
Any machine acting as a domain controller will have port 389 open (Kerberos). Therefore, identify the domain controller(s) with the following nmap script:
nmap -p389 -sV <target>
Once you Identify a domain controller, run the ldapdomaindump tool with compromised credentials against the domain controllers:
ldapdomaindump ldap://IP ADDRESS:389 -u 'DOMAIN\username' -p 'password123'
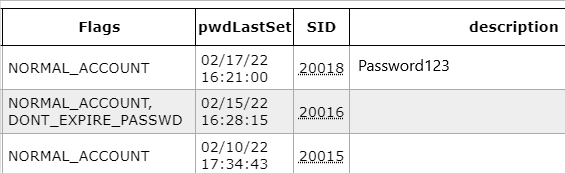
This will provide you with a few html files including all domain trust, account, ACL, and policy information. Look in to the domain_users.html file under the "Description" field and look for anything that looks like a password. In the image below, you will see "Password123" in the description field.
Now take those credentials and try crackmapexec with them to check If they are domain admin accounts.
crackmapexec smb <IP ADDRESS> -u 'domainadmin -p 'Password123'
If you see a "Pwn3d!" message in the output of this command, then you know you have domain admin!

